If you’ve used Let’s Encrypt, Caddy, Certbot, or Cloudflare Tunnel, you’ve already relied on ACME — even if you never touched it directly.
ACME is the reason HTTPS can be automated today. This post explains what the ACME protocol is, why it exists, and how it actually works under the hood.
What Is ACME?
ACME stands for Automatic Certificate Management Environment.
It’s an open protocol that allows a server to:
- Prove control over a domain
- Request an SSL/TLS certificate
- Renew that certificate automatically
All without human interaction.
Before ACME, certificate issuance was manual, slow, and error-prone. ACME turned TLS into an API.
Why ACME Exists
Old world:
- Buy certificate
- Upload CSR (Certificate Signing Request)
- Click email links
- Download files
- Install cert
- Repeat every year
Modern world:
textcert expires → ACME renews → no downtime
ACME exists to make HTTPS:
- Automated
- Cheap (or free)
- Scalable
- Default
That’s how Let’s Encrypt made HTTPS ubiquitous.
Who Uses ACME?
- Let’s Encrypt (primary user)
- Caddy
- Certbot
- Traefik
- Kubernetes cert-manager
- Many hosting providers
If a tool says “automatic HTTPS”, it’s almost certainly using ACME.
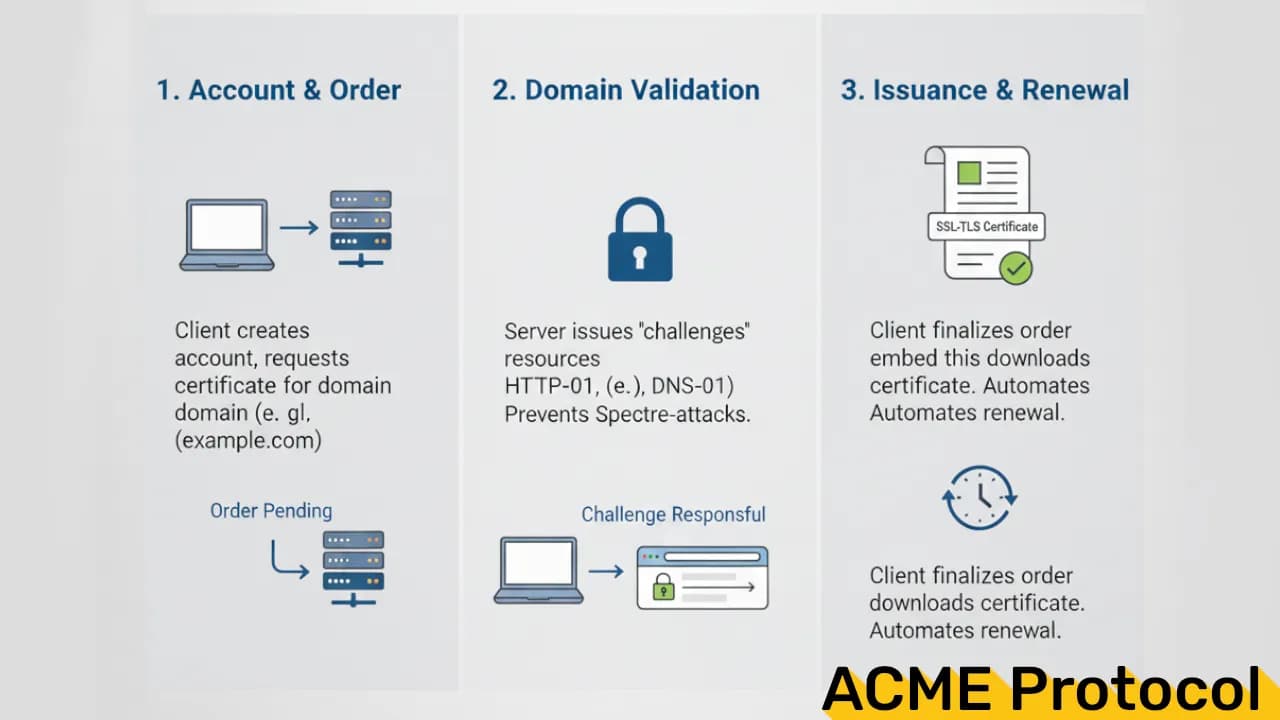
High-Level Flow
ACME is a client–server protocol.
- ACME Client: your server / tool (Caddy, Certbot)
- ACME Server: the CA (e.g. Let’s Encrypt)
Flow:
- Client asks for a certificate
- CA says: “prove you control this domain”
- Client completes a challenge
- CA verifies it
- Certificate is issued
- Client installs it
- Client renews it later automatically
Domain Validation Challenges
ACME doesn’t care who you are. Only one question matters:
“Do you control this domain?”
HTTP-01
-
Client places a token at:
path/.well-known/acme-challenge/<token>
- CA fetches it over HTTP
- Works only if port 80 is reachable
Simple, common, but not great behind firewalls.
DNS-01
-
Client adds a TXT record:
path_acme-challenge.example.com
- CA checks DNS
- No ports needed
- Required for wildcard certificates
More complex, but more powerful.
TLS-ALPN-01
- Special TLS handshake on port 443
- Less common
- Used in specific setups
Why Certificates Are Short-Lived (90 Days)
This is intentional.
Short lifetime means:
- Less damage if a key leaks
- Faster revocation recovery
- Forces automation (no manual renewals)
ACME assumes:
“If renewal isn’t automated, you’re doing it wrong.”
ACME and Security
ACME itself does not weaken TLS.
- Same crypto
- Same trust model
- Same certificate chains
The only difference:
- Humans are removed from the loop
Which actually reduces mistakes.
ACME vs “Buying a Certificate”
There’s no technical difference in trust.
Browser sees:
Valid certificate
Trusted CA
Correct domain
It doesn’t care whether:
- You paid money
- You used Let’s Encrypt
- You renewed manually or via ACME
Trust comes from the CA, not the workflow.
Where ACME Stops
ACME handles:
- Domain validation
- Issuance
- Renewal
ACME does not handle:
- Organization validation (OV)
- Extended validation (EV)
- Identity checks
That’s by design.
Final Thoughts
ACME is one of those rare protocols that:
- Solved a real problem
- Didn’t overcomplicate things
- Quietly changed the internet
Most HTTPS today exists because ACME made certificates boring — and boring is exactly what security infrastructure should be.
If HTTPS feels automatic now, that’s not magic. That’s ACME doing its job.
Album of the blog: